Complex processes require new solutions
With the help of so-called lifecycle management, an approach is created to simplify the administration of a system through operation to decommissioning, as well as to decommission systems and resources again if necessary.

Requirements for today's industrial networks have changed significantly in recent years. If you look back just a few years, you will see that the individual systems of a building, such as video surveillance, fire alarm systems, access control or even the HVAC system (heating, ventilation, air conditioning), were in most cases completely separate in terms of network technology.
It is not uncommon for a separate network infrastructure to be installed for each system. The multiple laying of network cables or the installation of multiple network components such as switches is usually also affected by the installation.
Counterproductivity quickly became apparent with regard to resources and clear planning. The following section explains why this is no longer sufficient from today's perspective or to meet the changed requirements. For existing infrastructures, there are a number of things to consider with regard to reengineering and lifecycle management.
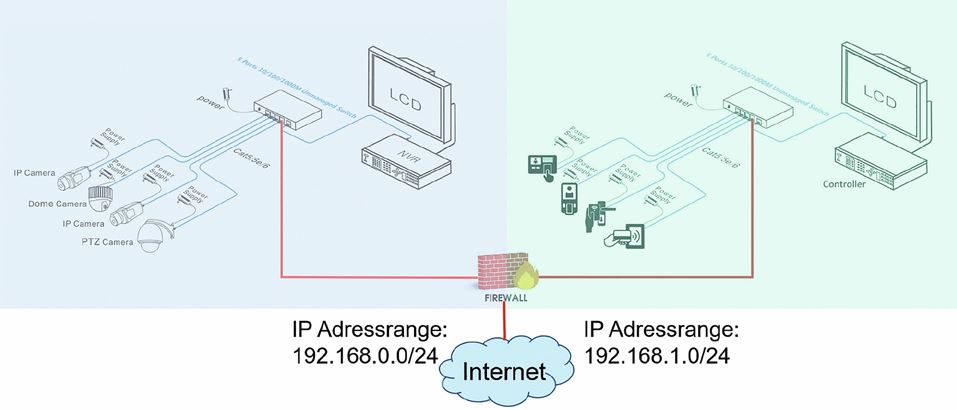
As shown in Figure 1 (see below), both systems have the same IP address range. As long as these two systems are operated separately, this operating mode works well and reliably. However, the requirements for the current systems have changed fundamentally. Today, convenience counts as well as functionality. For example, customers want to be able to access the various systems from a central location. Companies are also no longer prepared to finance multiple network infrastructures. With the help of modern network components, several systems can be operated simultaneously and securely on the same physical infrastructure, which massively improves the cost/benefit situation.
As a result of this requirement, it is necessary to connect these two systems together in terms of network technology. Since several devices now have the same IP address, the systems will inevitably misbehave. Because of this requirement, the existing networks must be "re-engineered". According to the current best practice approach, all the different systems, also called "trades", must each be "packaged" into their own network segment.
Network segmentation
Figuratively speaking, one of the two "houses" with the same postal address is given a new street name. This enables the post office to deliver the parcels, in this case the digital parcels, correctly on the network again. This measure is also referred to as segmentation. This makes it possible for network communication to now run via a central point and thus to define exactly which device is "allowed" to communicate with which end device. Another advantage of segmentation is the resilience of the entire infrastructure. If, for example, a cyber attack were to occur and such a segment were to be compromised, such an attack - if the firewall is configured correctly - would at most "only" have an effect on the affected segment; the others would at best not be affected and the company would continue to operate.
Advantages of professional lifecycle management
If we now take a look at lifecycle management, it quickly becomes clear that this also makes a major contribution to cybersecurity. In a management process of this kind, companies are first advised as to what IT components are required in order to be able to operate a company. In a second step, the appropriate components are ordered and made available.
The next step is to ensure effective operation. This involves, for example, the regular updating of the software. Every product is discontinued one day by the manufacturer and no longer supported. In such a case, for example, security updates are no longer provided. Here, lifecycle management helps to identify such components and replace them at an early stage.
Decommissioning of old components
Accordingly, the next step is based on the professional decommissioning of the old component and its dismantling to ensure migration to the new components. Controlled dismantling is very important in this respect to ensure that old systems are not "forgotten" and thus pose an existing danger.
From here on, the cycle starts all over again: Outdated and unpatched systems (systems that are not operated with the latest security updates) provide an immensely large and uncontrollable attack surface for cybercriminals. Once this basis has been created, one can turn to preventive maintenance (predictive maintenance). Here, digital sensors are placed in the entire infrastructure, but at the necessary points, which record and collect data and conditions around the clock.
If this data is systematically recorded and evaluated, conclusions can be drawn about the condition of the infrastructure. Accordingly, for example, it is recognized when a hard disk is approaching the end of its life, so that it can be replaced proactively before a crash occurs and the system comes to a standstill. With the help of such a functioning maintenance concept, significant contributions are made to avoiding downtimes and keeping downtimes low. This fundamentally optimizes maintenance, since effectively only those components need to be replaced that are demonstrably faulty or on the verge of collapse. In addition, an analysis can be planned for off-peak times so that the impact on the running system can be kept as low as possible.
This technical article appeared in the printed issue SicherheitsForum 1-2022.
You want to read the articles of this issue? Then close right now here a subscription.









