Privacy by Design
Everyone has been talking about data protection, and not just since PRISM & Co. The rapid development of networked mobile applications, social networks, cloud computing and business intelligence has already called for new concepts to protect personal data.

Many companies see data protection (privacy) primarily as a legal and organizational issue and choose a top-down approach to achieve compliance with valid laws. Privacy by Design (PbD), on the other hand, assumes that data protection cannot be ensured downstream through legal regulations, but must be implemented above all where personal data is stored and processed. In other words, where top-down approaches often do not yet consistently penetrate: in product and software design.
Basic principles of Privacy by Design
The Privacy by Design concept was significantly influenced and developed by the Privacy Commissioner of Ontario, Dr. Ann Cavoukian. It aims to make data protection the "default mode of operation" and thus ensure users' control over their personal data. To achieve this, PbD relies on seven basic principles, the implementation of which has also been endorsed by the Federal Data Protection
and Public Relations Officer Hanspeter Thür demands.

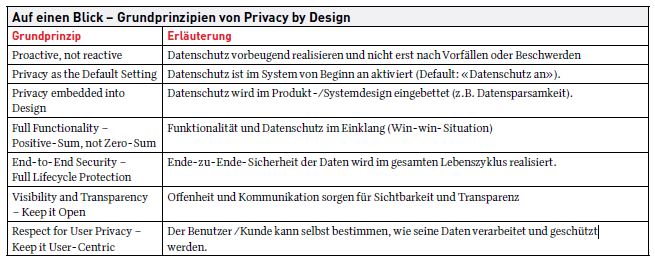
- Proactive, not reactive:
Data privacy and data security concerns must be implemented proactively and preventively - i.e., as early as the planning stage - and not only when risks have already occurred or even only after incidents or complaints. In this way, Privacy by Design prevents irreversible facts from being created.
- Privacy as the Default Setting:
In order to achieve maximum privacy protection, individuals should not have to take action on their own initiative. Rather, systems must be set by default so that no personal data is processed without explicit consent and appropriate protective measures.
- Privacy embedded into Design:
By embedding data protection in the design and architecture of products or systems, it becomes a core functionality rather than an add-on.
- Full Functionality - Positive- Sum, not Zero-Sum:
Functionality and data protection are not contradictory. Rather, Privacy by Design focuses on ensuring both the protection of personal data and full functionality as far as possible through early, holistic planning.
- End-to-End Security - Full Lifecycle Protection:
The protection of personal data extends over its entire lifecycle: from the initial capture of the data to its deletion. At each station in the process, appropriate measures must ensure the necessary security.
- Visibility and transparency - Keep it open:
Openness and communication ensure visibility and transparency - and thus the necessary verifiability of all systems and processes involved in the processing of personal data.
- Respect for User Privacy - Keep it User-Centric:
Privacy-friendly default settings and user-friendly options ensure a user-centric design. Users determine how their data is processed and used.
Consequences
For the development of software applications and systems, these principles mean that data protection, just like all other functional and non-functional requirements, for example quality, security and reliability, must be taken into account as early as the requirements analysis and design stage. This applies not only to the applications and systems themselves, but also to processes surrounding development and data transfer. Personal data must be stored and transferred securely. Furthermore, role and rights concepts as well as authentication procedures must be tailored to ensure that data access and data use comply with privacy guidelines. The requirements of the guidelines must also be met, especially with regard to user participation and transparency. To ensure this, a project manager or developer should always have the appropriate expertise.
Protection needs analysis
A protection needs analysis helps to determine whether and which personal data are processed and provides information about the required degree of PbD implementation. A wide range of organizational measures and supporting methods and technologies are available during the development process: Encryption, access control, anonymization and pseudonymization, data avoidance and data economy, and automated data deletion after an agreed period.
The Security Development Lifecycle (SDL), for example, takes data protection and PbD requirements into account. As part of this development process, the impact of new services and products on user privacy is assessed, among other things. This is in line with the European Privacy Impact Assessment (PIA) requirements.
Existing systems
For existing systems that were initially developed without a focus on data privacy, Privacy by Redesign can help. In this process, the existing systems, strategies, and processes should be reviewed and adapted so that they meet the data protection requirements.
This can mean changing functionalities within systems, but it can also mean a complete renewal of systems through an IT transformation that integrates privacy as a fundamental principle. However, this subsequent implementation of Privacy by Design can become difficult, if not impossible, in complex environments, depending on the system design. Dependencies and inflexible data structures can make Privacy by Redesign a tall order. In an emergency, this can lead, for example, to the complete CRM system of a group having to be replaced because the data of former customers cannot be deleted for technical reasons.

Privacy by Design: not yet widespread
Privacy by design is required wherever personal data such as name, address, place of residence, e-mail address, telephone, bank details, whereabouts, IP address or health data are stored or processed. This happens not only in the systems of companies with a large amount of customer or user data, such as financial service providers, insurers, search engines, and social networks; smartphones and modern cars now also process a large amount of this data.
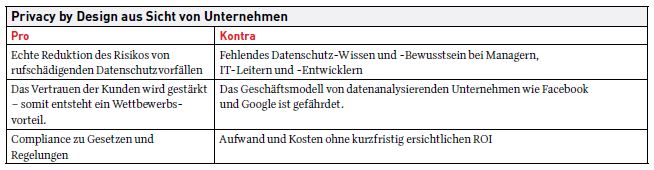
Nevertheless, Privacy by Design has so far only been consistently implemented in a few products and systems. For example, the search engine ixquick does not store IP addresses of users. Some data warehouse systems do not allow data mining down to the individual level, but only down to clusters with more than ten people, and also do not allow lists of individuals to be exported. Another example is the so-called body scanners at airports: until some time ago, these devices often showed detailed body contours and even gender characteristics. In order to protect the privacy of the persons scanned, systems have now been developed that only show the position of suspicious objects on the body without revealing any further details. There are several reasons for the reluctance to address the issue of privacy by design: First, data protection knowledge and awareness are often present in the data protection or legal department, but not among managers, IT directors and developers - i.e., where people primarily work with personal data. In addition, many managers do not attach any importance to data protection, since it initially only entails effort and costs, but no return on investment (ROI) that can be seen in the short term. Often, data protection is only practiced on paper, or companies try to transfer responsibility for data protection to customers and users. On the other hand, companies prioritize economic benefits from the analysis and use of extensive personal data and would also accept the penalties that will be levied if Privacy by Design becomes mandatory with the new EU General Data Protection Regulation. In particular, data-analyzing companies like Facebook and Google see Privacy by Design as a threat to their business model. If they had to implement PbD consistently, numerous analyses for advertising purposes would no longer be possible without further ado. For this reason, these companies are also resisting the proposal for the EU General Data Protection Regulation and are engaged in intensive lobbying.
Opportunities for companies
However, as a result of legal regulations and increasing compliance requirements alone, the topic of privacy by design will continue to gain massive importance and explosiveness. In the long term, the protection of personal data can become a real competitive advantage for companies, as customers and users begin to demand privacy-friendly products and turn their backs on data-collecting companies. Effective data protection and PbD measures can help to significantly reduce the risk of reputation-damaging data protection incidents and boost customer confidence - a real competitive advantage. Therefore, there are no alternatives to Privacy by Design for companies that want to develop "privacy-friendly" products and software.









