Malware disguised as Corona statistics
One click on the Corona statistic - and it's done: Cybercriminals exploit the theme to spread malware. This is disguised in a fake statistics card.
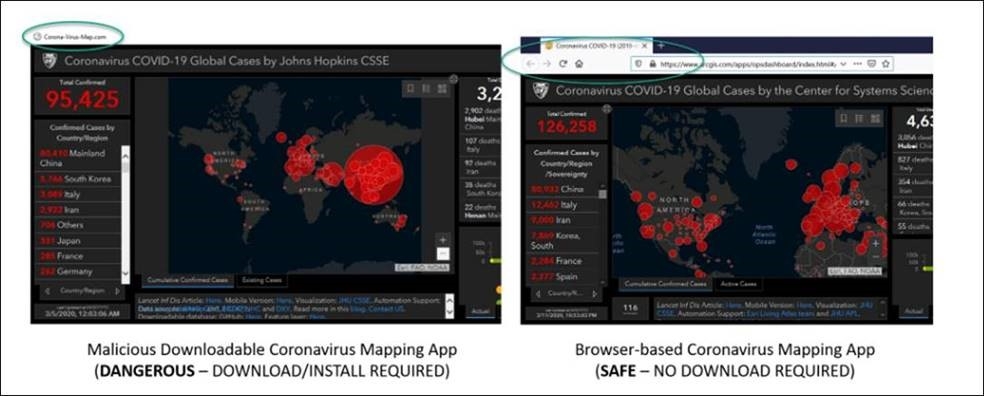
Who wouldn't want to be fully informed at the moment about how and where the virus is up to its mischief the most? And already it has happened. The St.Gallen cantonal police therefore point out that cybercriminals are currently using a fake coronavirus statistics map as malware. It is the popular map of the "Center for Systems Science and Engineering (CSSE)" of John Hopkins University (JHU). This card is infected with the so-called "AZORult" malware and then offered for download as an app (.exe file) on various platforms. The photo shows the difference between the malware version and the real card. So watch out - do not download this app!
These Corona stats are okay
Those who would like to gain insight into the Corona statistics can find the relevant information here:
Worldwide: Here it goes to the safe Covid-19 statistics.
Switzerland: If you want to look up the Corona case numbers for Switzerland, you will find the following on the website Corona Data found what they were looking for. The website is maintained by 34-year-old chem computer scientist Daniel Probst. The figures compiled by the doctoral student at the University of Bern are said to be more up-to-date than those of the Federal Office of Public Health.
Note on Corona Data: This website only works with HTTP (Hypertext Transfer Protocol). Better respectively more secure would be the HTTPS (Hypertext Transfer Protocol Secure); this hypertext transfer protocol works with an encrypted connection between the operator of the website and your browser.
Dangerous Covid-19 apps - stay away from them!
Avast has found several applications related to Covid-19 that have been classified as malicious. None of these applications are distributed via official app stores, but via SMS, web URLs, or social engineering. The types of malware range from ransomware, to spyware, to banking Trojans, the security vendor writes. Two examples of dangerous apps:
Covid19 / Coronavirus Tracker: This app is classic ransomware that locks out the owner of the smartphone and demands a ransom of 100 to 250 Bitcoins to unlock it.
Corona live 1.1.: This app abuses the official Samsung Health app icon for its own purposes and, once installed on the smartphone, sometimes has the ability to access the location, contacts, and camera of the infected device, as well as read SMS messages. In addition, the hacker can take photos and record audio and check running apps, to name a few examples. The data is reported back to a URL host, which in turn is connected to other malware samples.
Tips to protect yourself from malicious applications
The following three tips should be followed by users to protect themselves from malicious coronavirus applications:
- Uses websites instead of applications. Visiting a website is usually safer than installing an app on the device. In fact, most of the information that apps provide comes from websites anyway, which is why it makes sense to go directly to official websites, such as the World Health Organization or at the Robert Koch Institute, to inform.
- Installs apps from official app stores only. The vast majority of malware is distributed via unofficial third-party stores. Uses the Google Play Store or the Apple App Store for app installations.
- Get a second opinion. Before you install a new app, it's a good idea to check out its download numbers and ratings. This will help you better assess whether the application is useful or not.
Sources: Cantonal police, rs, Avast









