CEO fraud remains a perennial issue for SMEs
CEO fraud continues to be one of the most frequently reported fraud methods to the BACS and increased from 719 to 971 cases last year compared to 2024. Last week, the BACS again received reports showing that the perpetrators are constantly refining their scams. They no longer rely exclusively on fake emails, but also on psychological manipulation and artificial intelligence. This week's review looks at how you can recognize the subtle warning signals in everyday working life.

In the hectic pace of everyday business life, emails from superiors often set the pace for priorities. When management issues an instruction, it is usually carried out quickly and without much questioning. It is precisely this reflex that cyber criminals exploit in CEO fraud. The attacks often occur in waves and affect SMEs or associations of all sizes. The fraudsters mainly use data from public sources. Companies, associations or municipalities that publish information about their employees or their team on their website or in social media are therefore the main targets.
It all starts with research
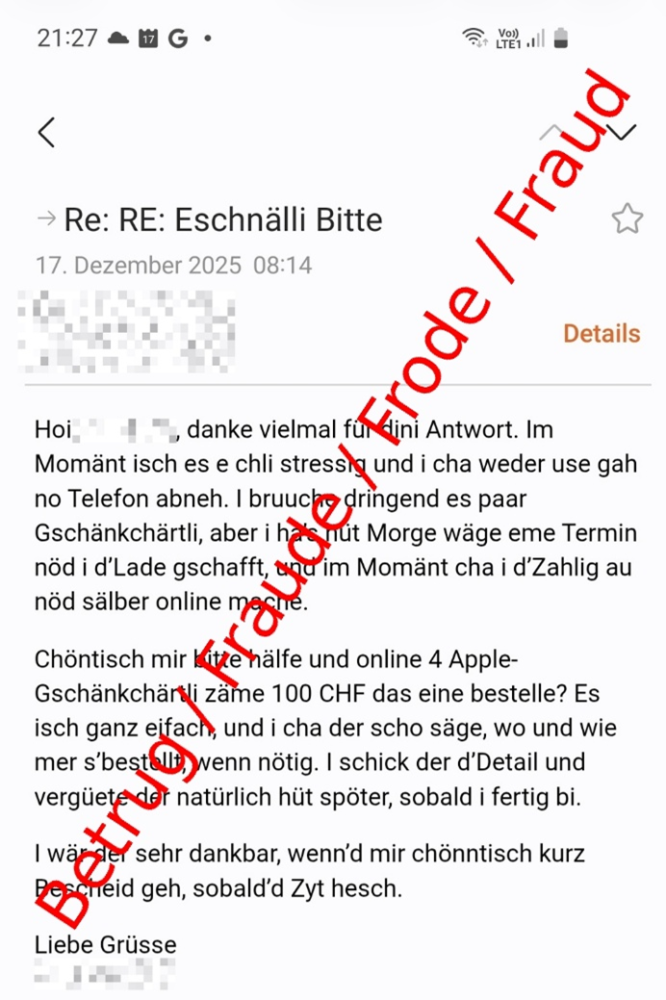
Authority meets time pressure
- An urgent payment to a foreign supplier, usually followed by a question about the outstanding or current account balance;
- The purchase of gift cards or vouchers for partners, which must be completed immediately.
The perpetrators build up psychological pressure. Phrases such as «I rely on your discretion», «I am incredibly grateful» or «Make the payment immediately» are intended to prevent the employee from complying with the usual security requirements or asking questions.
New variant via WhatsApp and with AI
Law firms again and again
Recommendations
The BACS advises companies to set up technical and organizational barriers:
- Four-eyes principle: For payments and changes to master data (e.g. a supplier's new IBAN), it is essential to enter a collective signature or approval by another person.
- Verification via a second channel: If you receive a request for payment by e-mail - especially if it is «urgent» or «secret» - call the client. Do not use the number in the e-mail, but the number you know.
- No exceptions: Clearly agree that safety processes must not be circumvented, even (and especially) in the case of instructions from the boardroom. Healthy skepticism should be seen as a strength in the corporate culture, not as disobedience.
- Marking of external e-mails: Configure your email server so that emails from external senders are clearly marked in the subject or body (e.g. «EXTERNAL»). This makes it immediately obvious if an email is supposedly from the internal CEO but was actually sent from an external address.
Source: BACS









