Separation locks: conceptual approach
As part of an access control concept, or at best already in the higher-level security concept, access protection must also be strengthened as a result of increased security requirements.
In most cases, measures such as the allocation of access rights and regulations are no longer sufficient. Even if these are supported and extended by checking various criteria, such as possession (e.g. card), knowledge (e.g. PIN) or biometric features (e.g. fingerprint). The corresponding regulations of access are then to be supported by further measures. These include systems for the separation of persons. The aim is to prevent the authorized entry of one person into a high-security area, such as a data center, from being "joined" by other and thus unauthorized persons. This cannot be achieved with conventional access controls at doors or even airlocks - they are not separation systems. Strict balancing can also be circumvented without a separation system.
Measures in the concept
As mentioned above, the basic principles that also apply to separation systems must be laid down in a security or access concept. This requires various structural, organizational and personnel measures. Their interaction must be defined as requirements for a system to be specified later within a conceptual design. These include:
- Conduct a risk analysis that identifies hazards from the environment and surroundings and an assessment of hazards arising from criminal activity and terrorism.
- Definition of security or protection zones that are staggered from the outside to the inside based on their different security requirements. A cascaded access system with staggered protection zones is more economical due to the plurality of security measures and makes more sense for the operational process within the respective property than martial measures in one place.
- Allocation of access authorizations to persons assigned to the respective protected zone. Here, it is particularly important to limit the number of authorized persons, which can be realized by the principle of separation of functions.
- Definition of responsibilities within access control. The person or persons - the principle of "as few people as possible" also applies here - assign access authorizations and define access times.
- Definition of time slots. Depending on the operating hours of the respective areas, it is necessary to define at which time access is permitted or not.
- Preservation of evidence via the access control system, where it must be determined which data is recorded upon entry and exit from the corresponding zone. Data protection requirements must be observed.
- Reaction in exceptional situations, such as technical malfunctions, overcoming attempts or in the event of fire or panic. Instructions for action or intervention plans must be stored, as these situations can predominantly only be handled by personnel.
In practice, unfortunately, it happens far too often that singulation systems have their difficulties in operation. One asks oneself, "What was the cause?" It could be design or planning errors, or difficulties during construction due to changes in the architecture, for example. Or the operation of the plant is too complicated for the users. A multitude of reasons that, unfortunately, are usually not always directly attributable and are also difficult and, above all, expensive to remedy in retrospect.
Practical tips for separating systems
The following are some measures to illustrate how best to approach the implementation of singulation systems.
First: Most of the time, the customer has already oriented himself on the market. They think they know what they need by studying product brochures. Unfortunately, this is not the case in most cases. Many boundary conditions and interfaces, such as the architecture, the necessary personnel throughput, the required fire and burglary protection, etc., are not taken into account. Our motto here is: "You don't pick products, you make demands on the market."
Second: Therefore, the creation of a functional description of the desired functions and processes is important. The aim here is to describe the development path, taking into account all influencing factors. This can be done in a flow chart, but also quite conventionally in prose. This includes describing entry and exit from the facility, escape route options, consideration of technical faults and all important operational requirements. After all, it may also be that material transport is required, for example. This explanation not only serves as a template for the planning of a separation system, but is also a good aid for the subsequent testing of this system.
Third: Contents of this description are to be created functionally and must clearly elaborate the project-specific differences. The following aspects should serve as a guide:
- Type and variety of functions: In addition to the requirement for singling out people, is there transportation through the facility, if necessary, or do separate routes exist, e.g., airlocks?
- Doors: There are usually complex requirements placed on the doors of separating systems - with door operators, automatic locking systems, hold-open systems or fire and smoke protection requirements. The equipment can influence each other, so that the desired functions cannot always be mapped together. This is where safety versus security comes into play.
- Authorization Means: What should be used to access the system in a controlled manner? In most cases, cards that are used to control the online access control system are the most common means. In addition, it may be necessary to open the door with a key or even to open the door remotely as an emergency or panic opening. Here, too, there are influences on each other; these interfaces must be taken into account.
- Separation technique: Depending on the respective separation technology, influences can also occur here. In the case of video separation in conjunction with light incidence through glass doors, for example, malfunctions can occur due to the formation of shadows inside the airlock.
- Biometric access control: There are still acceptance problems with many users, e.g., vis-à-vis iris scanners. Installation heights also play an important role - is operation equally suitable for tall and short people?
Fourth: It is now common knowledge that the cheapest offers are not always the best. But how do I manage to maintain the quality and thus the suitability of the product in correlation with the costs? The development of a criteria catalog with questions specially prepared for the bidder to ensure the important services has proven to be successful. After that, products can be compared well with each other and it is the quality and not only the price that counts.
Fifth: Documentation is always a good topic. This must be put out to tender in the desired quality and also demanded on the basis of this. The documentation is then clearly a component of the overall performance and corresponding final invoices should not be issued without submission and closer examination of the documentation documents.
Sixth: A system can be accepted in one way or another, but a separation system is a complex system and must be put through its paces in its entirety. This can only be done with a cross-trade function test in all operating modes. It is well known that with doors, problems are only encountered after some time. And this is usually no different with separating systems. A certain test phase should therefore be allowed in order to be able to detect such problems as well.
An example
An excerpt from the description of the transition to a data center will be used to show what requirements must be met by such a system.
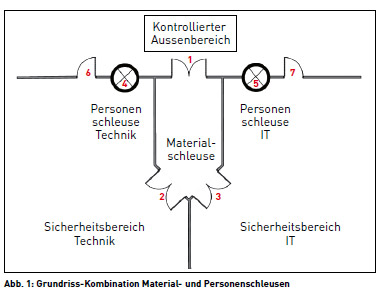
This is a system via which two groups (IT personnel and technical personnel) are guided separately to their destinations. For this purpose, one separation is provided for the IT personnel and one for the technical personnel. The two airlocks do not differ from each other in terms of their equipment.
For bulky objects, which cannot be brought in through the personnel airlocks, a material airlock is needed, from which the transport within the further protected zones is separated from each other - equivalent to the separation of persons.
Request personal locks:
- Separation of persons
- Safety turnstile
- Resistance quality RC2
- Lock is video monitored at the entrance and exit respectively
Request transport lock: The transport or material lock is used for the entry and exit of bulky goods. The airlock is designed so that it can be used by both technical and IT personnel. However, this is not possible at the same time. It is intended exclusively for use by authorized persons.
Material injection (using the example of technology injection)
- Basic status: Lock closed and locked, traffic light signal "green".
- Person (technical) with transported goods enters area in front of airlock (controlled outside area).
- Authorized person books at the badge reader of the outer door (1, see Fig. 1) .
- Video surveillance is started and connected to the control center.
- In case of green booking and locked inner doors (2, 3), opening outer door (1) and bringing the transported goods into the lock. Alarm is triggered if the door open time monitoring of three minutes is exceeded. Traffic light signal on "red".
- External door (1) can be kept open via the hold-open function. Door open time monitoring is set generously (3 min.)
- Exit of the authorized person from the lock again via the external door (1).
- Releasing the hold-open and closing the outer door (1) by authorized person - material lock closed.
- Empty space monitoring active, airlock incl. transport material, traffic light signal "red".
- The authorized person enters the security area via the technical personnel airlock (4) and is then located in front of the internal door of the technical equipment airlock (2).
- In case of green booking at the reader inner door technology material lock (2) and locked outer door material lock (1) and inner door IT material lock (3) - opening inner door technology material lock (2).
- The inner door of the material lock (2) can be kept open by keeping it open. Door open time monitoring is set generously (3 min.)
- Transport material is brought out of the airlock into the technical safety area. If the door open time monitoring of three minutes is exceeded, an alarm is triggered (can be set).
- Release of the hold open and closing of the inner door technique material lock (2) by authorized person.
- Video monitoring and connection is stopped as soon as the inside door of the technical material lock (2) is closed again.
- Empty space monitoring reports: no transport material, traffic light signal on "green".
Due to the arrangement of the material lock for both user groups, simultaneous use is not feasible. However, simultaneous entry or exit through the IT personnel airlock during material airlocking is possible.
Escape route from airlock
In principle, it is not necessary to escape from the IT and technical security areas via the material or personnel airlocks. Separate escape doors (6 and 7) are available for this purpose.
However, if you are in the material lock, it is possible to ensure escape via the outer door (1).
The following procedure shall be provided for this purpose:
- Person operates escape door terminal at the outer door (1) inside the airlock.
- Local alarming of the escape door terminal and reporting of the triggering to the control center.
- Video surveillance is already active due to the entry or exit (person in the airlock).
- Escape door terminal releases outside door.
- Person is able to get out of the airlock into the controlled outside area and continue to escape.
- Video surveillance and intrusion is stopped as soon as the escape alarm has been reset on site.
In the event of a malfunction of the respective airlock, the entry of persons and transports must be monitored by organizational safety measures (plant security staff).









