Remote access: a new standard should fix it
The security industry is very reluctant to apply remote access to customer systems. Until now, there has been no binding standardization describing services to customer systems in terms of security, duties and organization of the service provider. The European standards organization CEN-CENELC wants to close this gap with a new standard.

In connection with the European service standard for fire safety systems and safety installations (SN EN 16763) also raised the question of how to describe the services to be provided by Ferne. The association Euralarm elaborated a guideline for this purpose, which, however, is not obligatory.
The new European standard "Requirements for the provision of remote services for fire safety systems and security installations" describes how remote access can be provided. From the first contact with the system operator to the completed service in his system, a validated process is to be applied that prevents misuse and malfunctions as far as possible. Ultimately, the aim is to work more efficiently and save costs.
This standard corresponds to the European trend towards service standards in Europe. These are characterized by the fact that terms are defined and general descriptions for processes and services are standardized. They contain few measurable quantities and refer to product standards in which technical parameters, such as data interfaces or response times of data telegrams, are defined.
Expectations of the new standard
The standard is intended to enable the use of new technologies for remote access and to define the framework for operation and maintenance with remote access as intended. It is intended to be applicable to all security trades.
It obligates the service providers to comply with the set requirements, which are to be understood as minimum requirements. Plant operators should be able to assume that their security needs are covered before, during and after remote access.
The standard is intended to refer to adjacent areas of law such as data protection, contract law, national application guidelines, and certification of systems and employees.
The standard should be generally understandable and, where necessary, refer to existing standards. For example, ISO/IEC 9594 and ISO/IEC 27001 describe how an information security management system, authentication and the use of encryption are structured. On the other hand, there is a lack of implementation in the daily use of IT security. E-mails are still sent like postcards, readable by everyone and without a digital signature. With reasonable effort, any mail sender can set up a digital signature and also encrypt e-mails. The challenge is more on the side of the addressee, who must also consciously activate the security process in order to verify the mail, read it and send his encrypted reply. Under no circumstances should unencrypted e-mails to the plant operator contain a date and the type of remote access planned, let alone relevant security information.
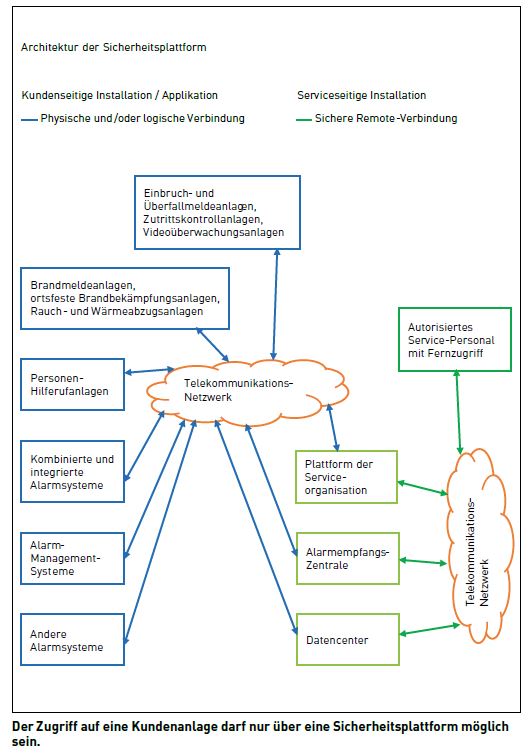
Controlled access to the customer plant
Access to a customer facility must only be possible via a security platform that performs the authentication and logs the significant events (see graphic). Under no circumstances may remote access by a service provider to the security system be possible directly via the Internet using a laptop or PC. Reasons for this are that
- damage can be done with stolen access data and corresponding software
- there is no centrally retrievable history in the event of a failed deployment.
A clear agreement on the access authorization of the service provider must be established in writing with the plant operator. Access to the customer's plant must be enabled by the plant operator. If operating parameters that are used to trigger condition-based maintenance are automatically transmitted to the service provider, this must also be specified in writing. Under no circumstances should an external system dock at the customer's plant and demand the release of customer data. The transfer must be controlled by the customer facility. The service provider must be able to prove to the plant operator at any time when remote access took place and what activities were carried out with it.
Application in practice
What services can be provided with remote access? With remote diagnostics, the service provider can reduce its response time and query the operating status of the customer's plant. Possible causes of malfunctions can be derived from this. Condition-based maintenance is also based on diagnostics in order to calculate the wear stock (e.g. degree of dustiness of the fire detectors).
With remote parameterization, customer parameters can be recorded and changed. If the functions of the safety system are changed in the process, a check must be organized on site.
The remote control can be used to reset event messages (alarm, fault). Or faulty system parts can be switched off if it is ensured that such shutdowns are reported on site and routinely reported to the responsible office.
Remote repair is more difficult and can actually only be limited to software and its operating parameters. Software system errors can be eliminated with a software download, provided this does not result in any change to the scope of functions. If the error removal or the software download is not possible, for example, due to faulty transmission, the initial state must be maintained. The same applies to the planned software update. If this involves adjustments to the functional scope of the plant, an on-site test is necessary and the plant documentation must be updated.
Also conceivable is remote instruction of a plant operator for operation of the plant, resetting of operating messages, elimination of fault messages and confirmation of any test functions.
Remote access test cases must be executed with technical presence in the object (e.g. siren test). It must be ensured that certain functions are never triggered in remote mode. This applies in particular to controlled interfaces for extinguishing systems, fogging systems, etc.
Services such as data maintenance or analysis are particularly feasible for video security systems and access control systems. Data protection must be observed here.
Current status of the standard
The current working paper also includes personal emergency call systems. These were explicitly excluded from EN 16763. In the meantime, a technical standard has been established for this segment: EN 50134:2017 Alarm systems - Nurse call systems. Nevertheless, it is questionable to include the personal assist call systems in this standard. In this area, completely different criteria already apply today. Just think of the Rega app, which can be used to locate hikers who have had an accident in the mountains.
Different requirements due to the various trades must be taken into account. Local guidelines also play a role here, and they still apply. In Switzerland, for example, the alarm must be ensured at all times during the planned maintenance of a fire alarm system. If necessary, with organizational measures on site. There are countries in Europe where such a regulation is missing and there is no need to include something like this in the standard.
The responses to the consultation on this standard so far show little interest in other countries in Europe. However, it is to be hoped that the next revised draft will find more resonance. It may still be years before the standard becomes valid.
Conclusion
Clear rules and written agreement are a necessity for remote access in security facilities. Remote access requires a security platform and clear security requirements for the service provider's personnel.
The ability to remotely access customer assets can very well support, but not replace, an on-site specialist.
If spatial or climatic conditions change on site, this can negatively affect the function of the safety systems and their components. Therefore, a visual inspection on site will still be necessary.
For its part, the system operator must take measures to prevent unauthorized remote access.
Author: Felix Hahn, Dipl. El.-Ing. HTL, NDS UF, former chairman of the SES Maintenance Committee and SES delegate to the Service Section of the Euralarm.