SaaS is trending, but so are the risks
Palo Alto Networks has released its latest "Application Usage and Threat Report. "The report, based on data from more than 7,000 enterprises worldwide, covers real-world trends in application usage and critical developments in how attackers are trying to infect enterprises.
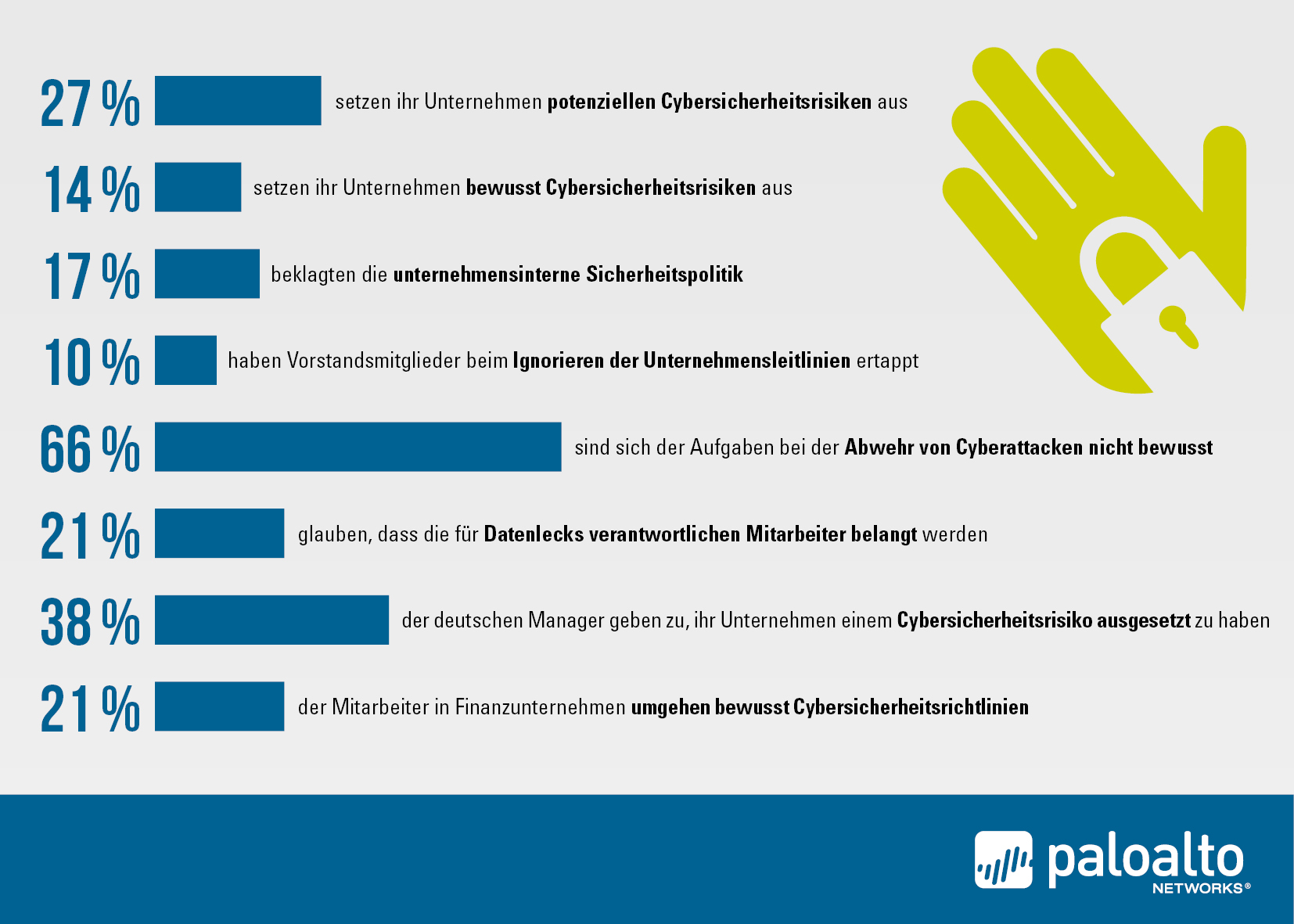
The results of the latest report from Palo Alto Networks underscore the rapid growth of software-as-a-service (SaaS)-based applications, the security firm writes. This has resulted in new risks and the threat of unauthorized access to sensitive data. The report also described global trends in the use of applications in high-risk categories, such as remote access applications.
Key findings of the report:
- SaaS-based applications are growing in popularity - the number of SaaS-based applications on enterprise networks increased by 46% from 2012 to 2015 and now exceeds 316 applications.
- Email attachments remain sources of infection - over 40% of email attachments carry risks.
- The use of remote access applications is widespread - there are currently 79 different remote access applications in use around the world, often used by cyber attackers as part of their operations.
- Tragedies in news or headlines are used for attack purposes - on average, six hours pass between a breaking news headline and its use for a spear phishing, spam or web attack.
- Known adversary profiles - There are currently three prominent groups engaged in cyber espionage and cybercriminal activities targeting government institutions and businesses across Europe and North America: Carbanak (Russia/Ukraine), Sandworm (Russia), and Shell Crew (China).
Recommended measures
- With the increasing popularity of SaaS applications, security teams should familiarize themselves with "shadow IT," a trend in enterprise networks whereby users access SaaS and other applications without IT's knowledge or consent. This can weaken security policies.
- The continued proliferation of malicious email attachments underscores the need for automated security measures. For example, a hidden executable that is accidentally activated by end users can be stopped automatically.
- The speed at which new threats evolve is constantly increasing. Automated attack tools help cybercriminals exploit new vulnerabilities within hours. To stop these attacks, automated measures for advanced threat prevention are required. These provide a comprehensive overview of the current status in the network and offer protection against known and unknown threats.
The Application Usage and Threat Report is available for download at Download available.
(Visited 97 times, 1 visits today)









