Heat traces reveal the password
Password theft doesn't just happen through software and social engineering - a thermal imaging camera can be enough.
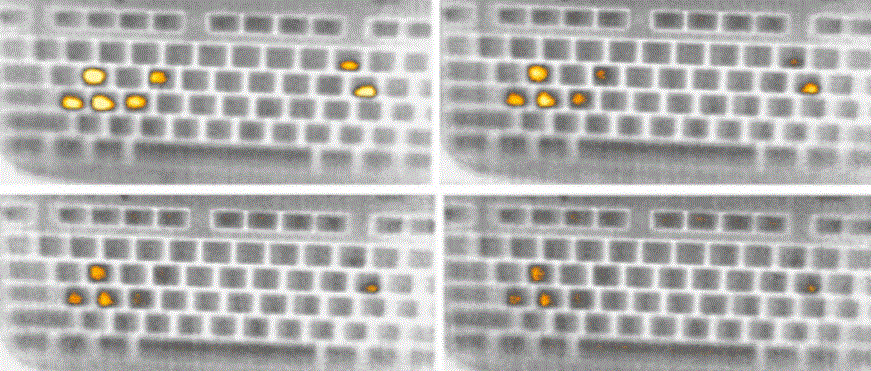
(University of California, Irvine)
According to a study by scientists at the University of California, the heat traces on commercially available keyboards are sufficient to pick up passwords. According to the researchers, entries from users of the two-finger search system are particularly easy to read. This unusual method of password cracking could be used in the field of cyber and industrial espionage.
Input still visible 10 min. later
"Underestimated risks lurk especially when it comes to password entry," says Thomas Uhlemann, Security Specialist at Eset. "While many are mindful of the unwanted shoulder look, no one is thinking about their own body heat - understandably so. That offers potential for cybercriminals - no matter how strong the password."
The researchers filmed the keyboards on which 30 test subjects had entered passwords. On the images, the pressed keys can still be recognized up to one minute after the input. And even laymen were able to reconstruct correct input sets and password fragments from these images in the next stage of the experiment. If two fingers were used instead of the 10-finger writing system, the thermal imprints were usually larger - and thus easier for potential attackers to construct.
2-factor authentication as a solution
The scientists recommend a number of countermeasures that should make password spying considerably more difficult or impossible. For example, the hand should be swiped across the keyboard after sensitive information has been entered, or a "thermal noise" should be generated by random input. Other countermeasures include using the on-screen keyboard and wearing heat-insulating gloves - a rather unrealistic scenario. "Much more practical is the use of secure 2-factor authentication solutions. These are convenient, easy to use and provide the maximum access protection," Uhlemann continues.
More about the study against password cracking: www.welivesecurity.com/deutsch/2018/07/13/passwortdiebstahl-heat-traces-tastatur/
Source: Eset









