Ransomware: How Defensive Are Swiss Companies?
How resilient are companies when they are targeted by ransomware such as "Wanna Cry"? A benchmark comparison of Swiss companies.

Advact got to the bottom of the question of defensibility with an attack on 42 Swiss companies. The sobering result: In 41 companies, at least one employee opened the email attachment infected with potential ransomware.
Infections take place via email
"Wanna Cry" once again demonstrates the impact of ransomware, according to the information security company. Even though the focus of "Wanna Cry" is strongly on automatic spreading by exploiting a vulnerability in Windows, many "Wanna Cry" infections take place via email - as is usual with ransomware.
Over 21,000 employees audited
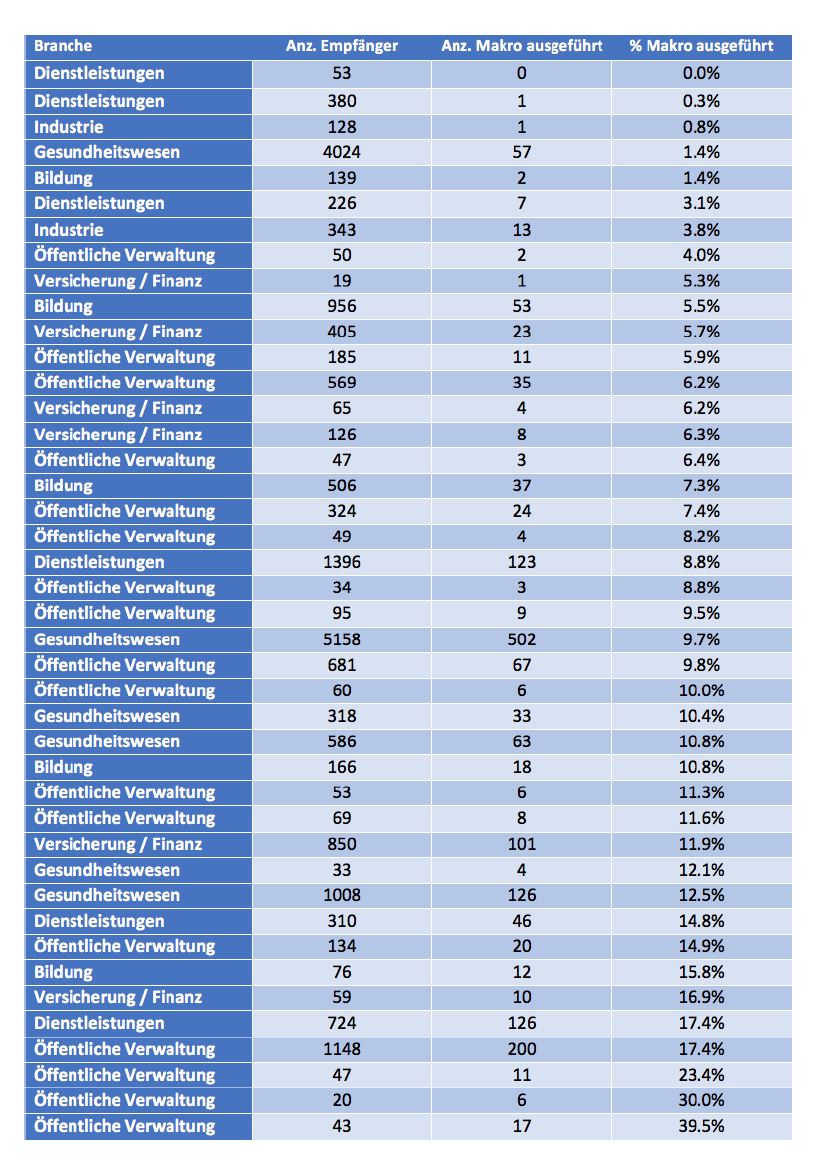
Switzerland seems to be relatively unaffected by the attacks at the moment. But what would happen if local companies, hospitals, etc. came under the spotlight? How would employees behave? Advact sent a ransomware email to a total of 21,662 employees from 42 different Swiss companies between May 8 and May 12, 2017, in agreement with the participating companies, and evaluated their reaction: 1,803 people executed the malware in the attachment and could have been infected with "Wanna Cry", for example. This corresponds to 8.3% of all email recipients.
After the evaluation, all employees were informed about the test. Through the experience and the education, participants learn to see through attack mechanisms more quickly and to react correctly in an emergency, as Advact emphasizes. The attachment benchmark thus offers much more than just a comparison of companies.
The anonymous results of the participating companies are shown below:
Tips to arm yourself
And because ransomware attacks are arguably inevitable, delivers Acronis a few tips to arm yourself against possible malware attacks:
- Always keep the operating system up to date. Updates are designed to ward off the latest known malware and close vulnerabilities.
- Do not open mails from unknown people or attached files whose source you do not know. This is still the most popular way of spreading ransomware.
- Secure your data with regular backups. The intervals of backups depend on how much new data you generate per day and how much you can do without in case of data loss without damaging your business. The backup should include the operating system information. In addition, the backup data must also be secured, because some ransomware versions attack this data as well.
- Use secure cloud offerings for added security.









