Regin spies on GSM mobile networks
"Regin" not only engages in cyber espionage activities, but also infiltrates GSM digital telephony networks. Thus, millions of GSM users could be spied on. Regin's backers have so far infected computers in at least 14 countries worldwide.

Infographics for "Regin
Mobile networks attacked
The most interesting feature of the Regin platform is its ability to attack GSM networks. Kaspersky Lab was able to obtain the activities of a GSM base station controller during its investigation. According to the analysis, the attackers have obtained credentials that allow them to take control of GSM cells of a large mobile operator. Thus, they could have gained access to information about which calls were processed by certain GSM cells. In addition, the attackers could have redirected these calls to other cells or activated neighboring cells, as well as unleashed other malicious activities.
The attackers behind Regin are currently the only known group capable of carrying out such operations. The analysis of Kaspersky experts has produced the following findings, among others:
- The focus of the attacks is against telecommunications companies, government institutions, financial institutions, research organizations, multinational political entities, and individuals whose field of research includes mathematics or cryptography.
- Victims were identified in Afghanistan, Algeria, Belgium, Brazil, Germany, India, Indonesia, Iran, Kiribati, Malaysia, Pakistan, the Republic of Fiji, Russia, and Syria.
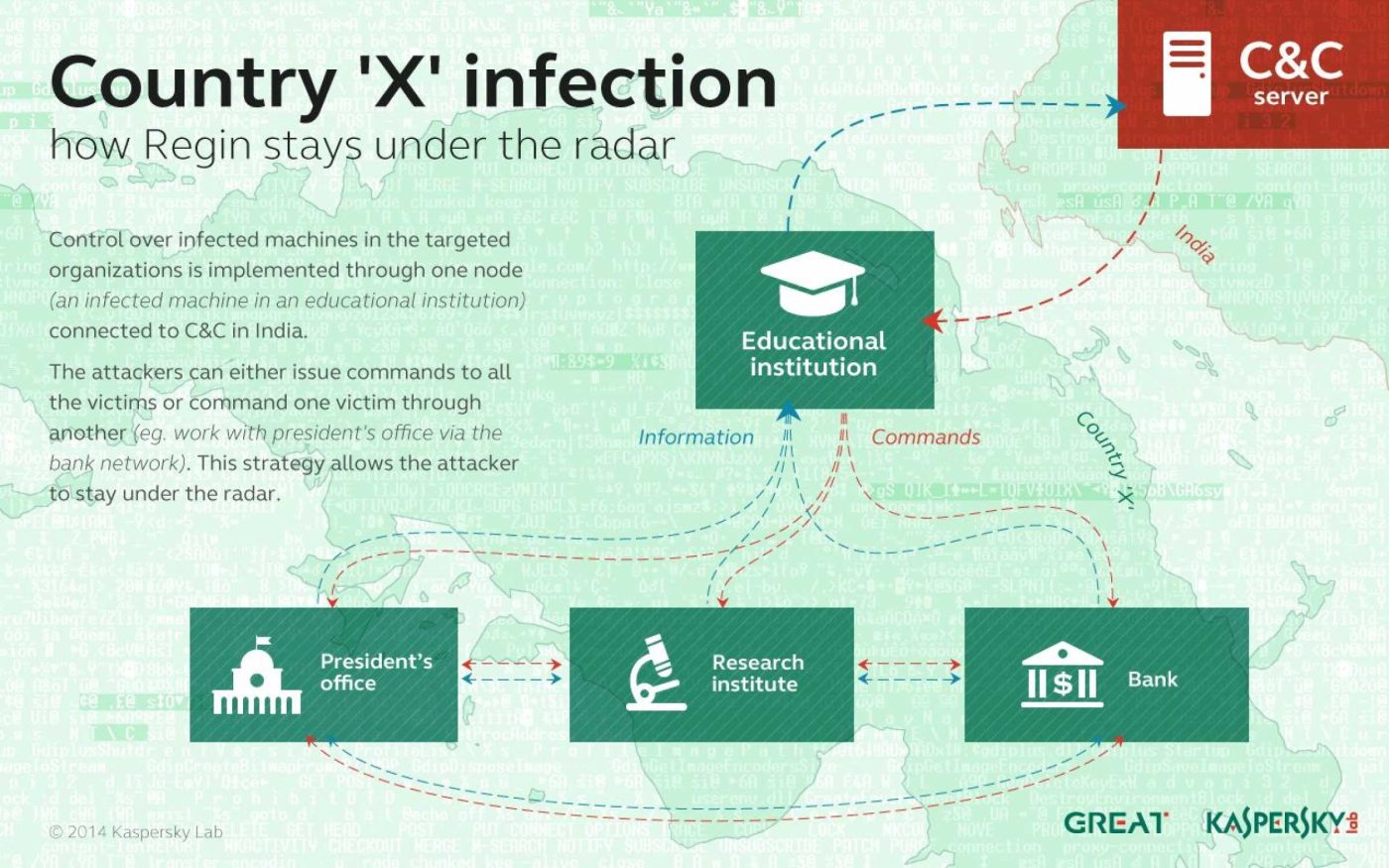
- The Regin platform consists of various malicious tools that allow attackers to gain access to an organization's entire compromised network. A highly complex communication method between the infected networks and command-and-control (C&C) servers enables covert remote control and data transfer.
- A main Regin module can monitor GSM base stations and steal data about GSM cells and network infrastructure.
- In April 2008, administrative access data was stolen within a month, which could have been used by those behind the theft to manipulate GSM networks in the Middle East.
- Regin's first samples were created back in 2003. Kaspersky Lab became aware of Regin in the spring of 2012. Since then, the IT security expert has analyzed the spying campaign. This analysis revealed that Regin is not just a single malicious program, but a complex platform consisting of numerous modules.
Here you will find the detailed analysis in English language.