Seven common cybersecurity myths
Myths are actually one thing above all: entertaining. However, there are also dangerous myths, like the one about cybersecurity. After all, a misconception about how a person can protect themselves digitally can sometimes lead to devastating security breaches. Therefore, it's time to debunk the seven biggest cybersecurity myths and better protect businesses.
Below are the seven common cybersecurity myths:
1 Password policies should include certain characters
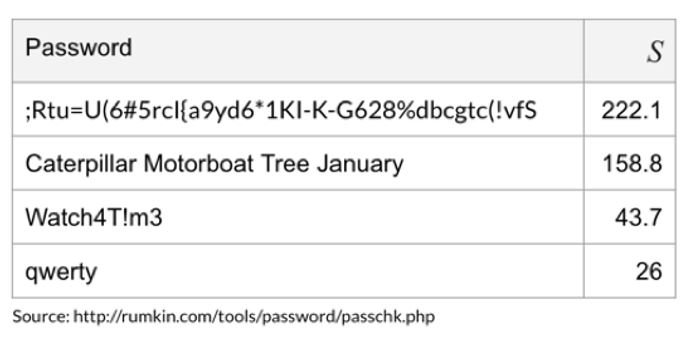
Special characters do not necessarily make a password more secure (see also article Secure passwords). The example in the table below shows that "Watch4T!m3" is a stronger password than "qwerty". However, "Caterpillar Motorboat Tree January" is three times stronger than "Watch4T!m3" even though it does not contain a single special character. Therefore, users should rather use longer passwords. Passwords with arbitrary special characters are not more secure, they only cause frustration for the user.
2 Multi-factor authentication prevents credential stuffing
Multi-factor authentication (MFA), while a cybersecurity tool, does not prevent Credential Stuffing. If a hacker tries to log in with incorrect credentials, the server responds with an error message. If the credentials are correct, the server requests a second authentication factor. This provides attackers with useful information. With the correct credentials, they can focus on schemes and gain access for the second authentication factor via social engineering, porting fraud, or SIM swapping, for example.
3 Without loss there is no fraud
Fraud is always fraud, even without data loss. As soon as a hacker performs a deception, for example by gaining access to an e-mail account, it is fraud, even if no damage has yet been done. There are definitely some types of attacks that first gain access and then wait. Nevertheless, it is fraud. So it is not uncommon for companies to be infiltrated long before they discover an attack.
4 Only a fraction of login traffic is automated
Enterprises underestimate the threat automated methods pose. With botnets, open proxy servers, compromised IoT devices, shared VPNs, and virtual servers, among others, attackers can launch distributed attacks using many millions of IPs from around the world. Existing countermeasures, such as web application firewalls, typically detect only a small percentage of attack traffic. Therefore, many countermeasures miss IPs with low traffic. Yet these are often the ones responsible for the most attack traffic.
5 Captcha stops bots
Captchas sometimes lead to increased blood pressure for people in front of the screen, but are not really an obstacle for attackers. There have long been human click farms - such as the Russian company 2Captcha - that offer fraudsters automated API access, solve captchas all day long, and thus make automated attacks possible.
6 Financial data and loyalty point aggregators take security seriously
Many users use a financial data aggregator to log into online bank accounts. This gives them an overview of their financial status and they don't have to log in every time they have multiple bank accounts. The same is true for loyalty point aggregators. However, the username and password for each account is first requested in order to link it to the aggregator. Hackers use stolen user/password pairs purchased on the dark web and test them in login forms of hundreds of websites via aggregators. Since many people reuse usernames and passwords frequently, this gives criminals access to thousands of user accounts using credential stuffing.
7 Cybersecurity is always stressful for individuals
This is wrong, because good cybersecurity works without the user even noticing or being affected. Behavioral biometrics run in the background and analyze keystrokes, touch commands, mouse movements, and device orientation to create and securely store a user profile. This data is analyzed and evaluated to calculate a regularity between the user's current behavior and their past and expected behavior. This prevents attackers from taking over accounts. This type of cybersecurity is much more secure than traditional logins.
Author: Bernd Achatz, Technical Director at F5 Networks, debunks business-damaging cybersecurity myths









